The Information Department, under the supervision of the General Manager’s Office, is responsible for coordinating information security and related matters. The specialized unit for information security is the Information Section, with the Information Section head serving as the security manager.
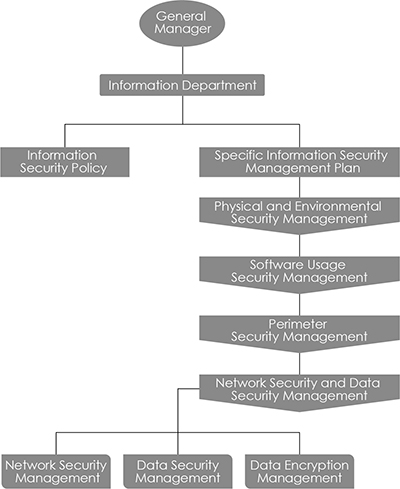
The scope of information security management in our company includes:
Computer equipment security and data center control management encompass hardware environment control, power supply, cable security, and equipment maintenance.
The disposal of physical information assets and equipment is managed uniformly by the Information Department in accordance with the procurement process and disposal procedures to prevent the leakage of personal information.
2-2. Software Usage Security ManagementOur company strictly prohibits and forbids the use of illegal pirated software. The software used within the company has been authorized by the respective vendors. Without prior consent from the company’s management and the head of the Information Management Department, downloading or installing software is strictly prohibited to avoid any infringement of intellectual property rights, violation of laws, or activation of malicious executables.
2-3. Perimeter Security ManagementTo achieve effective security control, personnel entering and exiting must carry identifiable identification cards and use personal fingerprint recognition. Information support or maintenance service personnel are only allowed access when accompanied by Information Management Department personnel or when granted specific authorization. Records of entries and exits should be maintained.
2-4. The resources for network security and information communication security management2-4-1. The resources for network security management :
The Information Department manages the network system to ensure its smooth operation. It installs devices such as firewalls and information security protection to prevent illegal intrusions that could compromise the company’s trade secrets and personal data. Additionally, the internal network and host systems retain complete records of all personnel logging in and out of the system。
2-4-2. Data Security Management:
Access control and data storage security are strictly enforced through password management and regular data and software backups. For critical information, a mechanism of storing data in remote locations is implemented.
2-4-3. Data Encryption Management:
A. To maintain the confidentiality, integrity, and availability of our company’s assets, document files and research development drawings undergo document data encryption management. Additionally, there is control over the usage of USB drives.
B. Any document taken out or provided to suppliers requires a decryption request process. Decryption can only be done with the approval and signature of the General Manager. Graphics files need to be archived by document control personnel before being forwarded by IT personnel via the company’s dedicated email.
| Solution | Content | Results |
|---|---|---|
| Network Security | 1. Implement a network firewall to block external cyberattacks. 2. Establish endpoint protection to prevent computer viruses and hacker intrusions. 3. Install antivirus software on computer equipment. 4. Set up SSL certificates for the company website. | *Antivirus software installation on computer equipment: 100% coverage. *Firewall setup and updates in the plant: 100% completion. *Antivirus software updates: 100% completion. *SSL certificate setup to enhance website security.。 *To ensure information and network security, a total of NT$601,648 was invested in 2025. |
| Data System Security | 1. Establish a data backup mechanism, backing up important system data and regularly conducting restoration drills.。 2. Virtualize important application systems and back them up daily. 3. Implement document encryption software. | *Host system backups: 100% completion. *Important data backups: 100% completion. *Virtual host restoration drills: 4 irregular drills per year. *Number of leaked confidential company documents: 0 incidents. |
| Educational Training | Conduct cybersecurity education and training for the company. External Training for the Information Security Officer and Information Security Personnel | *Periodic information security promotion and explanation sessions. *On March 8, 2025, personnel attended a 6-hour Information Security Training Course for Listed (OTC) Companies (FY 2024), organized by the Taiwan Academy of Banking and Finance. |
| Employee Information Security | Conduct cybersecurity education and training for the company. | *New employees are required to sign the Personal Computer Usage Policy. *A total of 36 new employees signed the Personal Computer Usage Policy in 2025. |